You are here
Verification and Certification Service Level Agreement
Requirements
This page details UC-specific requirements in addition to those detailed expressed for the Reference demonstration environment.
Hardware list
- Two Linux PC (for running the probe components server and client, the reasoner could be run on either of them.)
Software list
Components
- mSLAcert probe
Repositories
Reasoner
- The SLA reasoner.
Software dependency
In order to run the use case the following software is needed.
- Software:
- Python (>=3.3.x)
- Linux packages
- Additional libraries for RI
- sudo apt-get install python3-yaml
- sudo apt-get install python3-urllib3
- sudo apt-get install python3-tornado
- for the probe:
- sudo apt-get install iperf
- for the reasoner:
- expect - sudo apt-get install expect
-
convert - sudo apt-get install imagemagic
-
cupsfilter - sudo apt-get install cups
-
ps2pdf - sudo apt-get install ghostscript
- Additional libraries for RI
Executable permission are needed to run the reasoner.
Software installation
- Probe:
- On a Ubuntu-like PC, follow the instructions provided on the probe home page
Software configuration
Before running the components and the RI you need to configure the .conf files at ./conf/ directory.
mPlane RI:
You need to configure mPlane client as following:
- ./conf/client.conf
[TLS]
cert = PKI/ca/certs/"client-certicate".crt
key = PKI/ca/certs/"plaintext certificate.key
ca-chain = PKI/ca/root-ca/root-ca.crt
[client]
# leave registry_uri blank to use the default registry.json in the mplane/ folder
registry_uri =
# http://ict-mplane.eu/registry/demo
# workflow may be 'component-initiated' or 'client-initiated'
workflow = component-initiated
# for component-initiated:
listen-host = "IP of the machine where is launched the client" (exmp:192.168.3.1)
listen-port = 8891
listen-spec-link = https://"IP to where the spec are/IP Supervisor":8891/
registration-path = register/capability
specification-path = show/specification
result-path = register/result
# for client-initiated:
capability-url: "IP supervisor":8890/ (exmp:192.168.2.1:8890/)
- ./conf/supervisor.conf
[TLS]
cert= PKI/ca/certs/CI-Supervisor-FUB.crt
key= PKI/ca/certs/CI-Supervisor-FUB-plaintext.key
ca-chain = PKI/ca/root-ca/root-ca.crt
[Roles]
org.mplane.FUB.Components.mSLAcert_server = guest,admin
org.mplane.FUB.Agent.mSLAcert_Agent = guest,admin
org.mplane.FUB.Supervisors.CI_Supervisor_FUB = admin
Supervisor-1.FUB.mplane.org = admin
org.mplane.FUB.Clients.CI-Client_FUB = guest,admin
[Authorizations]
ping-average-ip4 = guest,admin
ping-detail-ip4 = guest,admin
tcpsla-average-ip4 = guest,admin
tcpsla-detail-ip4 = guest,admin
udpsla-average-ip4 = guest,admin
udpsla-detail-ip4 = guest,admin
msla-average-ip4 = guest,admin
msla-detail-ip4 = guest,admin
msla-AGENT-Probe-ip4 = guest,admin
[client]
# workflow may be 'component-initiated' or 'client-initiated'
workflow = component-initiated
# for component-initiated:
listen-host = "IP of the machine where is launched the supervisor" (exmp: 192.168.2.1)
listen-port = 8889
listen-spec-link =
# https://127.0.0.1:8889/(link is external)
registration-path = register/capability
specification-path = show/specification
result-path = register/result
# for client-initiated:
component-urls: "IP of component 1":8888/,"IP of component 2":8888/ (exmp: 192.168.1.1:8888/,192.168.4.1:8888/)
[component]
scheduler_max_results = 20
# leave registry_uri blank to use the default registry.json in the mplane/ folder
registry_uri =
# http://ict-mplane.eu/registry/demo
# workflow may be 'component-initiated' or 'client-initiated'
workflow = component-initiated
# for component-initiated:
client_host = "IP of the machine where is launched the client" (exmp: 192.168.2.1)
client_port = 8891 / 9911
registration_path = register/capability
specification_path = show/specification
result_path = register/result
# for client-initiated:
listen-port = 8890
listen-cap-link =
# https://127.0.0.1:8890/
You will have also to configure a clinet that will be used by ./reasoner_msla.sh
Components
- ./conf/component*.conf
[TLS]
cert = PKI/ca/certs/"Components-certicate".crt
key = PKI/ca/certs/"plaintext certificate".key
ca-chain = PKI/ca/root-ca/root-ca.crt
[Roles]
org.mplane.FUB.Clients.CI-Client_FUB = guest,admin
"add also the roles for all the other components, client, supervisor ect"
[Authorizations]
msla-AGENT-Probe-ip4 = guest,admin
"add the capability of your probe"
[module_mSLA_main]
module = mplane.components."name of python file"
ip4addr = 1.2.3.4
[component]
scheduler_max_results = 20
# leave registry_uri blank to use the default registry.json in the mplane/ folder
registry_uri =
# http://ict-mplane.eu/registry/demo
# workflow may be 'component-initiated' or 'client-initiated'
workflow = component-initiated
# for component-initiated
client_host = "IP of the supervisor" (exmp: 192.168.2.1)
client_port = 8889
registration_path = register/capability
specification_path = show/specification
result_path = register/result
# for client-initiated
listen-port = 8888
listen-cap-link = https://127.0.0.1:8888/
Repositories
- There are no repositories used for this usecase.
Reasoner
mSLAcert reasoner uses mPlane client, if it is different from the one configured, you need to add an additional link for it at the supervisor.
-
- ipaddressdest.in- each row contains the destination IP that have mSLAcert_Agent enabled.
- ipsupervisor.in- on this file is set the IP of the supervisor that the reasoner will use.
- measnum.in- on this file is set the default value is "0", please do not change this file.
- timemeas.in- on this file, measurement unit is set in seconds, the default value is 40 seconds.
Demonstration environment
To demo this use case are needed special hardware that can add impairments on the network (like modifying RTT, adding congestion, modifying jitter etc).
Step-by-step walkthrough
Before launching the components the configuration files are needed to be configured as in "Software configuration" part.
To run the CI components (with SSL), from the protocol-ri directory, run:
To run CI mSLAcert server:
export PYTHONPATH=.
./scripts/mpcom --config ./conf/component.conf
To run CI mSLAcert Agent:
export PYTHONPATH=.
./scripts/mpcom --config ./conf/component-agent.conf
To run mPlane client:
export PYTHONPATH=.
./scripts/mpcli --config ./conf/client.conf
To run mPlane Supervisor:
export PYTHONPATH=.
./scripts/mpsup --config ./conf/supervisor.conf
This will launch the supervisor.
To run mSLAcert reasoner:
./reasoner_msla.sh
Warmup:
First you need to make sure that all the component communicate with each other:
From the mPlane client connect to the supervisor and get capabilities:
|mplane|getcap https:"ipsupervisor":8890
After make sure all the capabilities are presented on the supervisor with:
|mplane|listcap
Trigger:
To see changes on TCP traffic the following network impairments could be used:
- High RTT (>=100ms)
- High jitter (>=30% RTT)
- Link congestion.
- Low SNR
- High BER
Observe:
You can choose the capability you want to run with: "|mplane| runcap cap-name" command. To fully test SLA, run tests based on RTT, TCP and UDP measurements:
There could be launched the SLA capability as:
|mplane|runcap msla-average-ip4
|when| = now + 40s / 1s
destination.ip4 = 192.168.1.2
source.ip4 = 1.2.3.4
ok
And get the results as:
|mplane| showmeas msla-average-ip4-0
Measurements could be performed and retrieved separately as well:
|mplane| runcap ping-average-ip4}
|mplane| runcap ping-detail-ip4
|mplane| runcap tcpsla-average-ip4
|mplane| runcap tcpsla-detail-ip4
|mplane| runcap udpsla-average-ip4
|mplane| runcap udpsla-detail-ip4
|mplane| showmeas [label-or-token]
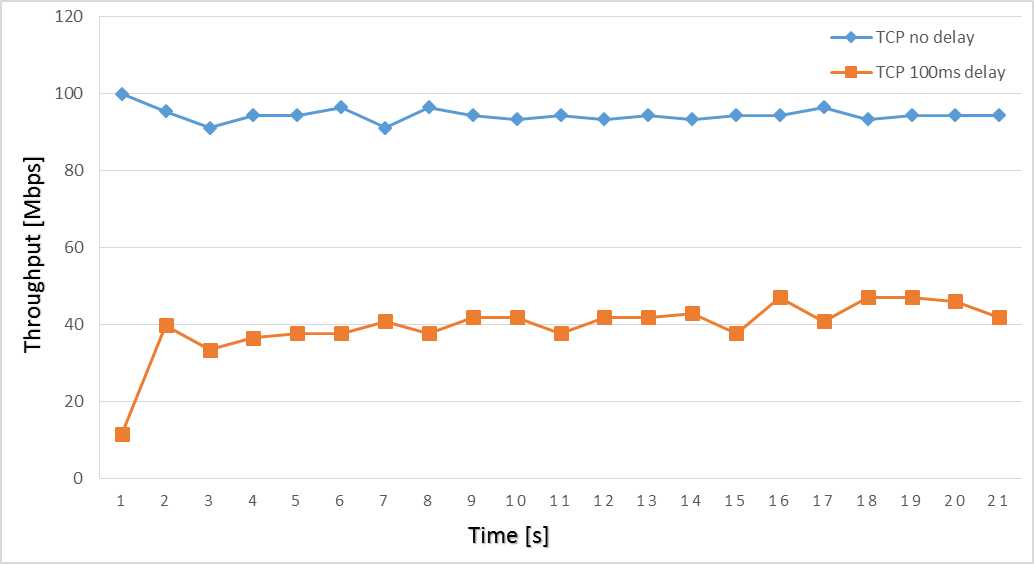
In a normal case with no interference there should not be a big difference between the throughput of TCP and the throughput UDP on the client side. If there are impairments on the network we would see degradation of TCP througput, incrementation of jitter etc.. To analyse more in detail the nature of the impairment on the network, other probes/ capabilities could be used. For example on high RTT, depending on your congestion algorithm you could see a difference of the throughput as show below:
Automatic running tests using the SLA reasoner:
The SLA verification could be done automatically by the SLA reasoner. The reasoner automatically tests SLA in terms of RTT, TCP throughput and UDP throughput and prints the results into a .PDF file. To run the reasoner you need first to add executable permission to the ".exp" files and to ".sh" file. Then from the terminal set on the path of the mother directory of the mPlane RI folder just run:
./reasoner_msla.sh
After the completations of the measurement all the results will be on a "IP address".PDF file of the mPlane RI directory. For more dettails on the settup and the code the reasoner please see the SLA reasoner web page.
